External service integration
Security management
In order to call a service from a widget, requestExternalResource must be
called. This method will send a request to the talentsoft application that will
act has a proxy. This is done order to manage the security aspect of the
integration in the backend.
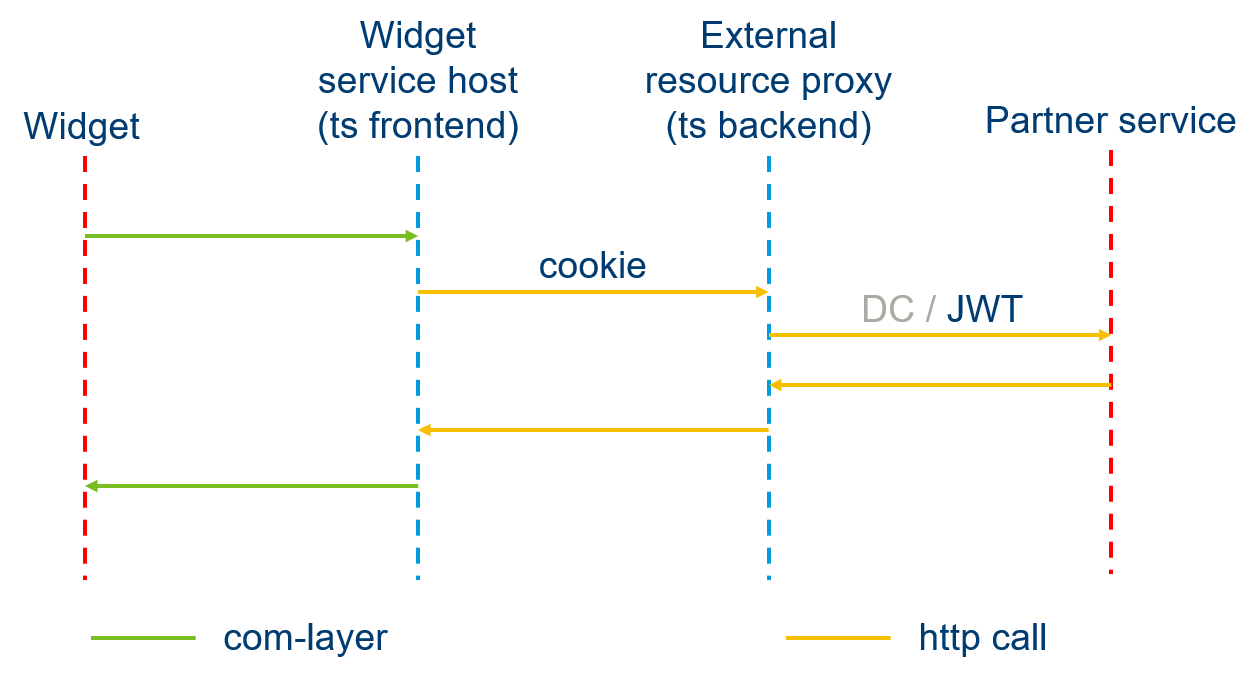
This means that the service must be compatible with one of Talentsoft's security modes. As of now, one security mode is available. It uses a jwt encoded with a symmetric key (using the HmacSha256 algorithm).
A client specific secret key must be configured in both system. In Talentsoft,
the secret must be included in the widget's client configuration with the
secretkey item. The securitymode item must be set to JwtSharedSecret.
Reading the token
In a case of an api call, the token will be included in the Authorization header of the request with a Bearer prefix:
Authorization: Bearer <token>
In a case of an autologin link, the token will be included in the querystring with the token key:
https://service.com/autologin?token=<token>
Validating the token
When receiving the jwt, the service must validate it before giving access to private resources. The signature should be checked using the shared secret. Many libraries exist for this. Please visit https://jwt.io/ to look for a library suitable for your platform.
The jwt token contains a set of claims which consist in a list of key/value pairs. Standard claims such as "expiration date" or "not before" should be validated automatically by the library.
The service should perform manually the following checks:
-
the issuer (
iss) istalentsoft.com -
the audience (
aud) matches the service's name as agreed with Talentsoft -
the custom
tenantclaim should match the client's name as agreed with Talentsoft
The name of the user concerned by the request should be included in the subject (sub) claim.